Jim explained to me that my site ninedarkmoons.com is NOT infected with malware, which is what GoDaddy confirmed last night. Jim had me go to Spamhaus.com and enter “ninedarkmoons.com”. It said my domain name is NOT infected. However, my IP address is still showing as having issues. Jim explained that one IP address can service many websites. It’s how providers like GoDaddy succeed in running so many sites. He likened it to an apartment building. It might have one street address, but many people live inside that street address. And if one apartment is found to be running a meth lab, it could give the whole building a bad name, even though all the other apartments are fine. Something like that.
April Fools Day snow covering neighbor Kathy’s flowers:
ORIGINAL POST:
Decided to check in with my website this morning, which I haven’t been doing much lately [even though I have like 10 posts I need to write]. Saw a message from my WordFence plugin [the number one plugin for WordPress site security] that said “Your site IP address xxx.xx.xxx.xxx [my IP address] is blacklisted by a spam filtering service. Details: Your IP address appears on the Spamhaus Exploits Block List (XBL) which is a realtime database of IP addresses of hijacked PCs infected by illegal 3rd party exploits. You can find out more by visiting the URL: http://www.spamhaus.org/xbl/”.
This has happened before, and turned out to be nothing, so I wasn’t that worried.
I went to Spamhaus [“the world leader in supplying realtime highly accurate threat intelligence to the Internet’s major networks”] and entered my IP address and got this [SCARY] message:
Results of Lookup
xxx.xx.xxx.xxx [my IP address] is listed
This IP address was detected and listed 29 times in the past 28 days, and 4 times in the past 24 hours. The most recent detection was at Fri Mar 27 10:15:00 2020 UTC +/- 5 minutes
This IP address is most likely a web server running some sort of CMS system (like Drupal, WordPress and so on), where a virtual host (customer web site) has been compromised into providing forwarding links to malicious web sites. The infection is often caused by malware called Stealrat
WARNING These listings are particularly pernicious, and if the web site isn’t cleaned and disinfected as per the instructions below, chances are that it will be relisted again almost immediately. Repeat listings will result in removal being prohibited.
This IP address corresponds to a web site that is infected with a spam or malware forwarding/redirection link.
In other words the site has been hacked and is serving up redirection links to spam or malware. It is also almost certainly sending spam too. [I had never seen this message before – starting to panic!!!]
We recommend that you review instructions below so as to prevent this happening in future. Once done, you can use the self-removal link below.
The infected host name is “investmentfundingnow.com“, and this link has an example of the malicious redirect: “https://investmentfundingnow.com/keratotomy/blader_potgun.html” Depending on the infection type, there may be dozens more malicious redirection pages under investmentfundingnow.com. [PANIC PANIC PANIC!!!]
WARNING As the link is known to malicious, browsing that link is at your own risk.
IMPORTANT If investmentfundingnow.com is not your host, there is nothing you can do to fix this problem: contact your hoster and have them fix it.
So, since investmentfundingnow.com is definitely NOT my hosting provider, I immediately contacted GoDaddy, who is. They verified the malware and submitted a trouble ticket to their tech team to get the malware removed and to secure my site. Even though I have 3 layers of security protection on my site, including 2FA, a lot of WordPress plugins have been hacked lately and if it’s one of the ones I use, my site would be infected. So far none of the ones I use have been flagged as hacked, but earlier this week one of the plugin AUTHORS I use had 2 of his other plugins hacked, so I’m guessing that’s where this hack came from. I have temporarily disabled the plugin of his that I use, so parts of my site will be unavailable until I can do more research. Such a scary world. My site is super slow right now, taking forever to load pages, so I’m assuming that’s from the malware.
Hope everyone is staying safe and as happy as possible during these very stressful, surreal times.
Message from GoDaddy:
“We have started working on your case, but I am escalating it to a senior analyst to help me out here. We will get back to you shortly with an update.”
Message from GoDaddy:
“Hi there,
I’ve just finished doing a manual audit on your site and went through all files and did not find anything malicious. I also don’t see the site to be blacklisted anywhere.
What leads you to believe that your site is infected? Please send over any details which might help us in our investigation.
If you’ve received any warnings or notifications please supply them here in this ticket so we can take a look. Thanks! Talk to you soon.”
Today the SpamHaus message is saying something slightly different at the bottom. I sent GoDaddy all the info from the above blog post, as well as the new message at the bottom:
“The infected host name is “fastcomsupply.com”, and this link has an example of the malicious redirect: “http://fastcomsupply.com/wp-content/themes/twentyfifteen/mercy/lubberly_Berkeleyism.html” Depending on the infection type, there may be dozens more malicious redirection pages under fastcomsupply.com.
IMPORTANT If fastcomsupply.com is not your host, there is nothing you can do to fix this problem: contact your hoster and have them fix it.”
My IP address is no longer listed in Spamhaus’s XBL:
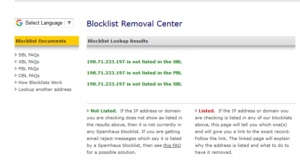


That is scary. I hope you can get it fixed soon.
Thanks, me too! According to GoDaddy my site is NOT infected. Who knows. I added some updates at the bottom of my post.